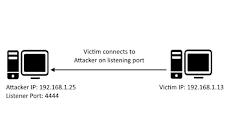
Reverse Shells

Proxychains is a tool that forces any TCP connection made by any given application to go through proxies like TOR or any other SOCKS4, SOCKS5 or HTTP proxies. It is an open-source project for GNU/Linux systems.
Essentially, you can use ProxyChains to run any program through a proxy server. This will allow you to access the Internet from behind a restrictive firewall, hide your IP address, run applications like SSH/ telnet/wget/FTP and Nmap through proxy servers, and even access your local Intranet from outside through an external proxy.
Proxychains even allows you to use multiple proxies at once by “chaining” the proxies together and to use programs with no built-in proxy support through a proxy.
Fire up your Linux Terminal
write the commands
$ sudo apt-get install tor
It will install the tor service in your kali machine.
After that you need to open the proxychain.conf file to edit it.
$nano /etc/proxychains.conf
it will open the file in the editor, so that you can edit the files.
here, you need to change the confriguation
and save the file.
now use these command
$service tor restart
$proxychains firefox www.bing.com
as you can see the proxychain service is start, so now let's go to the dns leak test to check our ip.
here you can see my ip.
Thankyou!!!
Comments
Post a Comment