Reverse Shells
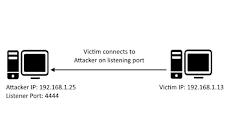

It's been a long since i posted blog, So in this blog i'll show you how i bypassed the OTP.
This is only for the educational purpose.
There are different ways by which we can try and bypass the login credentials with the help of different methods.
Today , i am going to tell you how you can bypass OTP using burpsuite.
Firstly, target any site or we can say select any site for the attack .
I selected ICICI bank website.
So First step :
First you need to configure your browser with the burpsuite and secondly, you need to configure your browser to use the Burp Proxy listener as its HTTP proxy server. To do this, you need to change your browser's proxy settings to use the proxy host address (by default, 127.0.0.1) and port (by default, 8080) for both HTTP and HTTPS protocols, with no exceptions.
NOTE : If the listener is still not running, then Burp was not able to open the default proxy listener port (8080).
So, here i entered my phone number for the OTP.
Intercept the request coming from the server.
Intercept: It capture the packet coming from the website or Server.
Now,we will captured the packet which was being sent over as a request packet to the server.
NEED TO KNOW : #In the response,the server gives error as (0) and
if the statement is successful it gives(1).
#Sometimes it gives error in code, so change it to Success.
#Sometimes, it gives incorrect , change it to Correct.
So now, i send the server request to the repeater and forward the post request to the intruder.
and intercept the post request. So here i got the OTP !!!
Finally, I got the OTP so here i use it!
Need To Know:
There are different methods to bypass OTP, many others were possible because of the lack lustre of the security personals where they do not apply security.due to which you can apply different methods to bypass OTP.
THANK YOU !!!!!
Nice blog Bro 👍
ReplyDeleteThankyou bro
DeleteGreat blog✨
ReplyDeleteGreat
ReplyDeleteIt's working keep it up champ
ReplyDeleteThank you brdr
DeleteGazab re londe
ReplyDeleteThank you!!
Delete